Security risk assessment template
What if you could build a security risk assessment (SRA) tool to assess and advise, accurately and objectively?
Security risk assessments are perfect to raise awareness and inspire action at scale, to mitigate threats to your organization.
Pointerpro is the 2-in-1 software that combines assessment building with personalized PDF report generation.
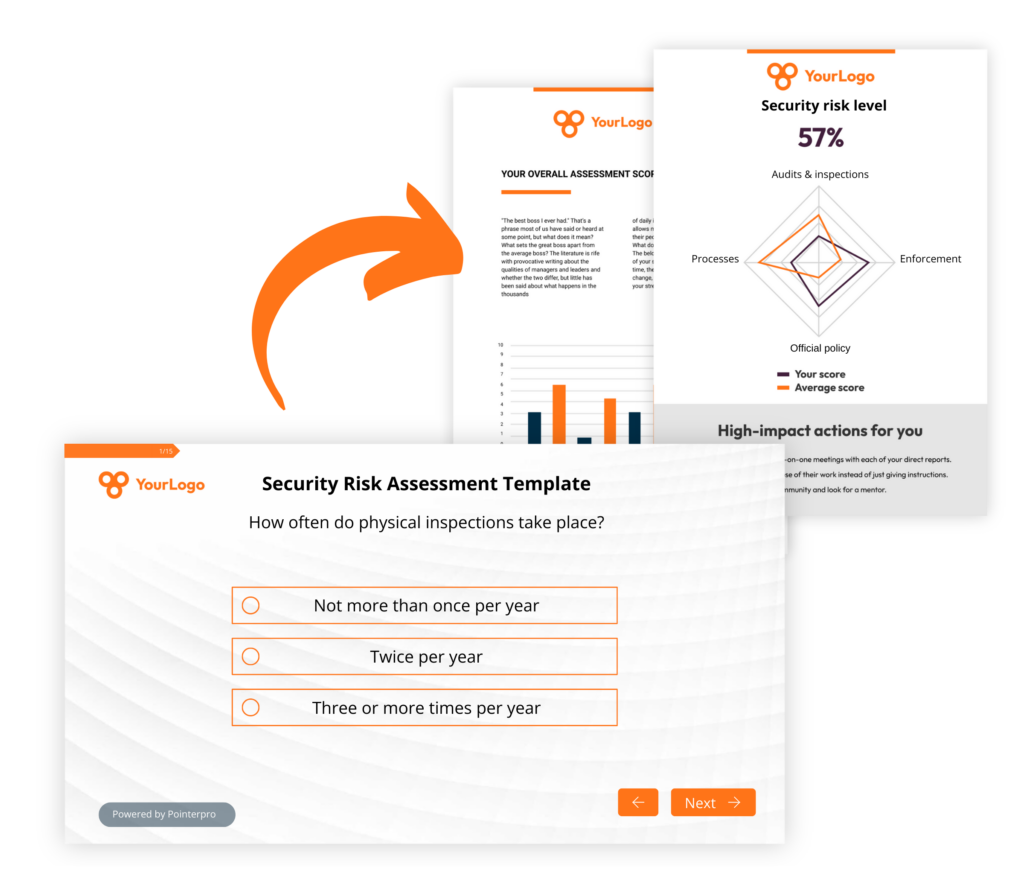
Security risk assessment tips: from questionnaire to feedback report
When developing a security risk assessment, your questionnaire serves as the foundation for understanding the responding organization’s security landscape, while the feedback report synthesizes the collected information, providing actionable insights and actionable tips, based on your expertise and know-how. Here are key guidelines to consider:
- Questionnaire simplicity: Craft clear and concise questions that cover the security domains you’re assessing. Ensure questions are relevant to the organization's specific context and industry.
- User-friendly interface: Provide an intuitive interface for the questionnaire to encourage participation. Include guidance to assist respondents in understanding and answering questions accurately. Also, consider giving intermediate feedback based on the chosen multiple-choice responses
- Actionable recommendations: Tailor a feedback report based on the responses to present findings in a digestible format for stakeholders. Provide clear and explicit next steps for risk mitigation.
- Stakeholder engagement: Involve key stakeholders in the assessment process to ensure relevance and accuracy. Encourage open communication channels to address any concerns or questions during the assessment. By aggregating response data from multiple responses, you
Important: When working with our clients at Pointerpro, we always insist they ask themselves three important questions before they actually start building it. Our colleague Stacy goes over them in the video below.
3 reasons to use Pointerpro as a security risk assessment tool
3 reasons to use Pointerpro as a security risk assessment tool
Interactive user experience
With the Questionnaire Builder you get to create an engaging assessment. How? With numerous design and layout options, useful widgets and countless question types.
Refined, score-based analysis
Our custom scoring engine helps you quantify the security risk levels. The result? An objective and very nuanced assessment of your respondents’ situation.
Automated feedback in PDF
Thanks to your setup in the Report Builder, respondents instantly get a detailed PDF report: with helpful charts, a personalized analysis of risks, and actionable tips.
1.500+ businesses worldwide build assessments with Pointerpro








50 security risk assessment example questions
Here are 50 of the best security risk assessment example questions divided into 5 categories:
- 10 physical security risk assessment questions for security, risk, or facility managers
- 10 facility security risk assessment questions
- 10 supply chain security risk assessment example questions
- 10 environmental security risk assessment example questions
- 10 cyber security risk assessment example questions
10 physical security risk assessment questions
- What is the current state of access control systems, and are they effectively limiting unauthorized entry?
- Are surveillance cameras strategically placed to cover critical areas, and is the footage adequately monitored?
- How often are physical security inspections conducted to identify vulnerabilities in perimeter defenses?
- Are there clear and enforced policies regarding visitor access and identification within the premises?
- What measures are in place to secure sensitive areas such as data centers, server rooms, or storage facilities?
- How is employee identification managed, and are badges or access cards required for entry?
- Is there a well-defined process for reporting and responding to suspicious activities or security incidents?
- What measures are in place to protect against environmental threats, such as fire, flood, or other natural disasters?
- Are there designated secure zones for the storage of valuable assets, and are these areas adequately protected?
- How is the security of parking areas and vehicle access controlled?
These security risk assessment template questions are designed to assess various aspects of physical security, covering access control, surveillance, employee and visitor management, incident response, and protection against environmental threats.
The questions aim to identify potential vulnerabilities and weaknesses in an organization’s physical security measures. This type of assessment should be conducted in collaboration with relevant stakeholders and may involve on-site inspections, policy reviews, and interviews to ensure a comprehensive understanding of the physical security landscape.
How to do a physical security risk assessment (SRA) in 5 steps
Developing a physical security risk assessment involves a systematic and multidimensional approach. It’s all about using comprehensive know-how. Begin by assembling a team with diverse expertise, including security professionals, risk managers, and facility managers.
- Define the scope and objectives of the assessment, ensuring clarity on the areas to be evaluated.
- Develop a comprehensive questionnaire covering aspects such as access control, surveillance, visitor management, and environmental threats. Design the questionnaire with clear, concise questions and provide multiple-choice answer options that capture the nuances of the organization's security measures.
- Distribute the assessment to relevant stakeholders. Pointerpro’s assessment platform offers a Distribution Portal, as a feature to delegate the distribution to respondents
- Follow-up: Once all assessment data are collected, it may be wise to perform a follow-up threat assessment, to evaluate the likelihood and impact of identified threats. Also recommended: Following up with on-site inspections to validate the information gathered.
- Report: Any security risk assessment is only as useful as the report it comes with. The report should summarize the findings and link them to actionable recommendations. Present the report to key stakeholders, fostering open communication and collaboration. Iterate the assessment process regularly, adapting it to evolving security threats and organizational changes.
This approach ensures a holistic evaluation of physical security measures, facilitating the identification and mitigation of potential risks to safeguard the organization’s assets and personnel.
The importance of security controls in a security risk assessment template?
A physical security risk assessment can encompass a range of security controls to evaluate the overall security posture of an organization. Here are 20 key security controls that can be assessed:
- Access control systems: Evaluate the effectiveness of systems controlling entry, such as key card access, biometrics, and PIN-based systems.
- Surveillance systems: Assess the placement, coverage, monitoring, and recording capabilities of surveillance cameras.
- Intrusion detection systems: Evaluate the effectiveness of systems designed to detect unauthorized access or intrusion attempts.
- Perimeter security: Assess the strength of physical barriers, fences, and gates protecting the organization's perimeter.
- Visitor management: Evaluate policies and procedures for managing and monitoring visitor access.
- Employee identification: Assess methods used for employee identification, such as badges or access cards.
- Security lighting: Evaluate the adequacy of lighting in and around the facility to deter unauthorized access.
- Security guards: Assess the presence, effectiveness, training, and responsiveness of security personnel.
- Physical inspections: Evaluate the frequency and thoroughness of physical security inspections
- Incident response plans: Assess the existence and effectiveness of plans to respond to physical security incidents.
- Secure areas access control: Evaluate access control measures for sensitive areas, such as data centers and server rooms.
- Alarm systems: Assess the deployment and effectiveness of alarm systems for various security scenarios.
- Environmental controls: Evaluate measures in place to protect against environmental threats like fire, flood, or extreme weather.
- Secure storage: Assess security measures for the storage of valuable assets, documents, or equipment.
- Biometric security: Evaluate the use and effectiveness of biometric security measures for access control.
- Key management: Assess policies and procedures for managing and securing physical keys.
- Training and awareness: Evaluate training provided to employees on physical security measures and emergency procedures.
- Parking area security: Assess security measures in place for parking areas, including lighting and access control.
- CCTV monitoring: Evaluate the effectiveness of personnel monitoring surveillance camera feeds in real-time.
- Secure zones designation: Assess the designation and protection of secure zones within the organization.
It speaks for itself that for each security control, a different set of questions applies. To keep stakeholders engaged, it’s better to develop a certain number of short security risk assessments that focus on a particular topic than to try and evaluate everything at once.
4 reasons to conduct a physical security risk assessment (SRA)
Conducting a physical security risk assessment is imperative for organizations seeking to fortify their defenses against a myriad of potential threats.
By systematically evaluating the vulnerabilities within the physical security infrastructure, such as access points, surveillance systems, and environmental controls, the assessment enables the identification of weaknesses that could be exploited by malicious actors. So, in summary, here are 4 key reasons why you should develop a physical security assessment.
- To identify weaknesses and vulnerabilities in an organization's physical security infrastructure, such as access points, surveillance systems, and environmental controls.
- To mitigate threats: Proactively identifying potential security threats and implementing preventive measures to reduce the risk of incidents, such as unauthorized access, theft, or vandalism.
- To comply with industry requirements: Ensuring adherence to industry regulations and standards that mandate specific physical security measures, particularly in sectors like healthcare, finance, or critical infrastructure.
- To protect assets: Safeguarding valuable assets, including data centers, equipment, intellectual property, and sensitive information, from physical threats and unauthorized access.
What Pointerpro clients are saying




Security risk assessment (SRA): Myths vs reality
-
Security is absolute:
- Myth: There is a common misconception that once a security risk assessment is conducted and measures are implemented, an organization is impervious to security threats.
- Reality: Security is an ongoing process; new threats emerge, and the security landscape evolves, requiring continuous assessment and adaptation.
-
One-size-fits-all approach:
- Myth: Some believe that a generic security risk assessment template can be universally applied across all organizations. It’s important to inject know-how in the questions and analysis that lead to your final report.
- Reality: Each organization is unique, and risk assessments should be tailored to its specific industry, size, and operational context for accurate threat identification and mitigation.
-
Technology solves everything:
- Myth: Relying solely on technological solutions, such as advanced cybersecurity tools, will address all security risks.
- Reality: While technology is crucial, a comprehensive security risk assessment must consider people, processes, and physical security alongside technological measures.
-
Risk elimination is possible:
- Myth: There's a misconception that the goal of a security risk assessment is to eliminate all risks.
- Reality: Complete risk elimination is impractical. The aim is to identify, prioritize, and manage risks effectively to an acceptable level within the organization's risk appetite.
-
Once-a-year assessment is sufficient:
- Myth: Conducting a security risk assessment annually is enough to address evolving threats.
- Reality: Threat landscapes change rapidly. Regular assessments, coupled with continuous monitoring and adaptation, are essential to stay ahead of emerging risks.
-
Only for large organizations:
- Myth: Small and medium-sized enterprises (SMEs) may believe that security risk assessments are only relevant to larger organizations.
- Reality: SMEs are equally vulnerable, and tailored risk assessments can help them identify and address security risks within their operational scope and resource constraints.
Dispelling these myths is crucial for fostering a realistic understanding of security risk assessments. Organizations must recognize the dynamic nature of security and embrace continuous, tailored assessments to effectively manage risks and protect their assets.
Common security risk assessment templates
- CIS Critical Security Controls: Outlines 20 critical security controls, offering a structured approach to enhance an organization's cybersecurity posture.
- FAIR (Factor Analysis of Information Risk): a quantitative risk analysis framework to assess and quantify information security and operational risks.
- Dread (Damage, Reproducibility, Exploitability, Affected Users, Discoverability): A simple but effective security risk assessment template or model, often used in software development.
- HIPAA security risk assessment template: Designed for healthcare organizations, ensuring compliance with the Health Insurance Portability and Accountability Act security requirements.
- PCI DSS security risk assessment template: Tailored for organizations handling payment card information, aligning with the Payment Card Industry Data Security Standard (PCI DSS).
Create your own security risk assessment
You may also be interested in
Recommended reading

Vlerick Business School digitalizes entrepreneurship development with Pointerpro [case study]
What do a top-tier international business school based in the capital of Europe and Pointerpro have in common? At the

Attain Global: How to do psychometric tests right and build a cutting-edge international business [case study]
In many countries worldwide, the pursuit of skillful and engaged employees is not so much a war on talent as
How youth development specialist Halogen reaches thousands of young Singaporeans with Pointerpro [case study]
Singapore, in Southeast Asia, is a global, economic powerhouse with a population of a little less than 6 million people.


