Cyber security risk assessment template
What if you could build a cyber security risk assessment tool to assess and advise, accurately and objectively?
Cyber security risk assessments are the first step to prevent disruption or even irreparable reputational damage to your business.
Pointerpro is the 2-in-1 software that combines assessment building with personalized PDF report generation.

What is a cyber security risk assessment?
A cybersecurity risk assessment is a tool to identify, analyze, and evaluate potential threats and vulnerabilities to an organization’s information technology systems, networks, and data.
The primary goal of a cybersecurity risk assessment is to understand the organization’s exposure to various cybersecurity risks and to develop strategies to mitigate or manage those risks effectively. Cyber security can be assessed at different levels. Cyber security questionnaires are an effective way to map out what an organization needs.
3 reasons to use Pointerpro as a cyber security risk
assessment tool?
3 reasons to use Pointerpro as a cyber security risk
assessment tool?
Interactive user experience
With the Questionnaire Builder you get to create an engaging assessment. How? With numerous design and layout options, useful widgets and countless question types.
Refined, score-based analysis
Our custom scoring engine helps you quantify the cyber security risk levels. The result? An objective and very nuanced assessment of your respondents’ situation.
Automated feedback in PDF
Thanks to your setup in the Report Builder, respondents instantly get a detailed PDF report: with helpful charts, a personalized analysis of risks, and actionable tips.
1.500+ businesses worldwide build assessments with Pointerpro






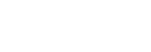


How to do a cyber security risk assessment?
Cybersecurity risk assessments are crucial in the process of identifying, evaluating, and mitigating potential security risks to your organization’s information systems and data. Here are some indispensable steps to conduct comprehensive cybersecurity risk assessments.
Preparational work:
- Identify assets: Make a list of all the assets that need protection, such as hardware, software, data, networks, and individual people or “user identities.” Categorize assets by importance and sensitivity.
- Identify threats: Identify potential threats and vulnerabilities that could affect your assets. Common threats include malware, data breaches, social engineering, and physical attacks.
- Define the scope: Cybersecurity is very vast. Therefore, clearly define the scope of each cyber security risk assessment. What are the systems, data, and assets to be assessed? Identify the boundaries and limitations of the assessment.
- Define the respondents: Not anyone in your organization will be able to provide the information you’re looking for. Therefore, consciously decide who you’ll administer different questionnaires to. If you’re assessing cyber secure behavior in general, it’s perfectly possible to distribute the assessment organization-wide.
The assessment itself and what it should divulge:
When you build your assessment, you should use scoring capabilities to do risk calculation and prioritization. You should attribute scores to the assets and potential threats you’ve identified. That way you can calculate what risks require the most immediate action.
- Your assessment should reveal vulnerabilities: The answers to the questions of your assessment should expose vulnerabilities and weaknesses in your systems and processes that could be exploited by the identified threats. It’s likely that you’ll need to follow up your questionnaire assessment with penetration testing and configuration reviews.
- Your assessment should reveal likelihood: Based on the respondent answers, you should be able to reveal the likelihood of different threats exploiting the vulnerabilities. For this calculation to be more sophisticated, it’s recommended to use formulas that take into account historical data, threat intelligence, and expert judgment to estimate the probability.
The cyber security risk assessment report:
A cyber security risk assessment will give you a clear view of the as-is situation. But of course, what matters ultimately are the actions taken to improve that as-is situation. The report you generate with your assessment could (and in many cases should) cover the following:
- Visualize findings: Create a comprehensive report that outlines the findings of your risk assessment, including the identified risks, their impact, likelihood, and mitigation strategies. Include different types of charts to get across clear messages.
- Mitigation strategies: Develop and document strategies to mitigate each identified risk. These strategies may include implementing security controls, policies, and procedures.
- Cost-benefit analysis: Evaluate the cost and benefits of each mitigation strategy to ensure they are cost-effective and align with your organization’s goals and resources.
- Risk acceptance: If certain risks are deemed acceptable after mitigation efforts, document the reasons to gain approval from relevant stakeholders.
- Risk monitoring: Establish a process for ongoing risk monitoring and management. Regularly review and update the risk assessment as the threat landscape evolves.
Note on continuous improvement:
Regularly review and update your risk assessment to account for changes in technology, threats, and the organization’s evolving needs.
Remember that cybersecurity risk assessments are an ongoing process, not a one-time task. Regular updates and adjustments are essential to maintain an effective security posture and protect your organization from emerging threats. It’s also a good practice to engage with cybersecurity experts or consultants to ensure a comprehensive assessment.
8 cyber security risk assessment template tips
No matter what questionnaire you’ll be setting up as a cyber security risk assessment, there are several essential cyber security strategy questions to ask yourself when you start developing a cyber security risk assessment template for your organization:
- Compliance vs. cyber risk: Are you only focusing on meeting compliance regulations, or do you want to actively manage cyber risks in the context of your business?
- Senior leadership involvement: Does senior leadership (C-level) support addressing assessment findings and view cybersecurity as an urgent priority?
- Human behavior: How are you addressing the human element in your assessment? Human behavior is a crucial factor in cybersecurity that you cannot fully control.
- Hacker’s perspective: When coming up with assessment questions, are you considering what a hacker would do and whether you’d be ready to defend against it?
- Accountability: Is it clear who is responsible for addressing vulnerabilities and mitigating risks in your organization?
- Business outcome: How is the assessment used as a tool to achieve your ultimate business goals and outcomes?
- The next assessment: When is your next assessment planned to ensure ongoing security against evolving threats?
- Recovery & continuity plan: What’s your business continuity and disaster recovery plan in the event of a hack or outage?
20 cyber security risk assessment example questions
Here are 20 of the best cyber security risk assessment example questions divided into 2 categories:
- 10 essential cybersecurity risk assessment questions for an IT manager to answer
- 10 cybersecurity risk assessment example questions to measure end-user awareness
10 cybersecurity risk assessment questions for an IT manager
- Are you able to provide an overview of the organization’s IT infrastructure, including the types of systems, applications, and data you manage?
- Have you identified the critical assets and data that the organization needs to protect, and what is their current security status?
- Do you currently have security policies, procedures, and controls in place, and are they enforced?
- Have there been any recent security incidents or breaches, and if so, were they addressed and resolved?
- Does the organization have user access management and authentication in place?
- Are there any known vulnerabilities or weaknesses in the IT environment that require attention?
- What measures are in place to monitor and detect security threats and incidents in real-time?
- How often are security assessments, vulnerability scans, and penetration tests conducted?
- Do you have a disaster recovery and incident response plan in place, and how frequently is it tested?
- Are there any compliance requirements (e.g., regulatory, industry-specific) that the organization needs to adhere to?
These cyber security risk assessment template questions focus on gaining a comprehensive understanding of an organization’s IT infrastructure, its current security posture, and its ability to manage and mitigate cybersecurity risks. They could be used by a cybersecurity consultant and allow an IT manager to provide a thorough overview of the organization’s cybersecurity practices, helping the external consultant assess current risks, vulnerabilities, and security measures.
The information collected serves as the foundation for developing recommendations and an action plan to enhance the organization’s cybersecurity posture.
10 cybersecurity risk questions to measure end-user awareness
- Do you receive regular cybersecurity training and awareness programs at work?
- Have you ever received suspicious emails or messages and reported them to the IT department?
- You are asked to create a password for a new work-related account. What do you do?
- A colleague from another company requests sensitive work-related information from you. What is your response?
- You step away from your desk at work for a break, leaving your computer unattended. What do you do?
- Do you regularly update your software, applications, and devices to ensure they are protected against security vulnerabilities?
- Are you aware of the organization’s data protection policies and procedures?
- Do you use a secure and encrypted connection (e.g., VPN) when accessing company resources remotely?
- You find an unknown USB drive in the office parking lot. What do you do?
- You suspect a security incident has occurred on your computer. What is your immediate response?
The overall approach of the cybersecurity behavior assessment, based on these 10 questions, aims to evaluate employees’ awareness and actions regarding cybersecurity practices within your organization.
These cyber security risk assessment template questions cover a range of critical cybersecurity areas, including training, incident reporting, password management, data protection, physical security, and more.
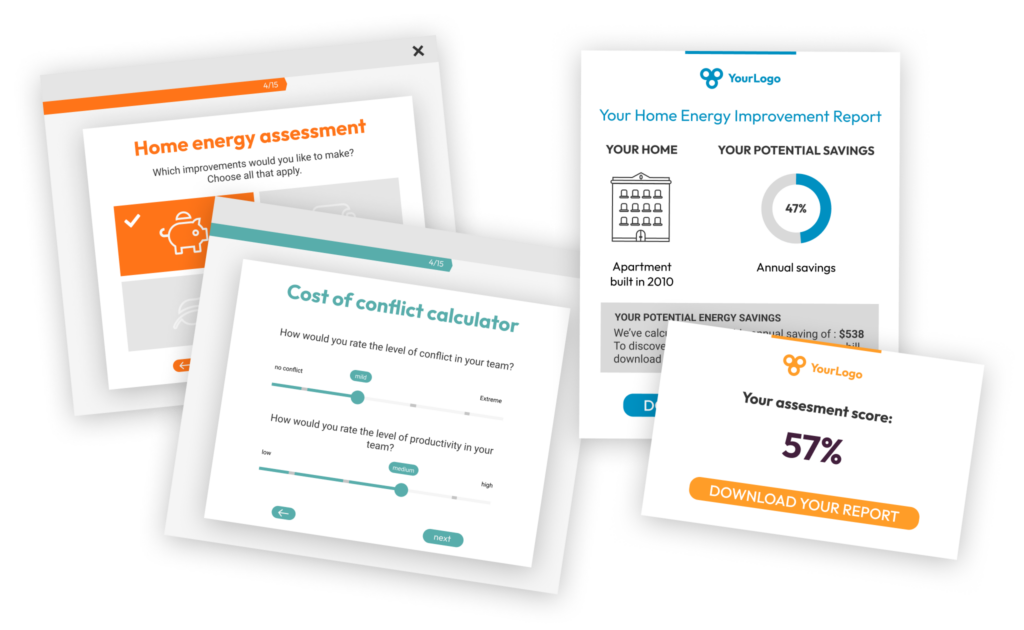
Score your cyber security risk assessment questions for better insights
With Pointerpro, you apply formulas so respondent input is calculated and measured.
The result? Relevant cyber risk analyses are automatically molded into visual reports for yourself and each respondent.
Learn more about “custom scoring” in the video below.

How to assess a zero-trust security posture
Safeguarding the 5 pillars
Assessing a zero-trust security posture involves evaluating an organization’s readiness and implementation of the five fundamental pillars of zero trust. Zero trust is a security framework that operates under the assumption of no inherent trust in any user, device, or network, even if they are inside the corporate perimeter.
These are the key principles to follow:
- Verify identity (Identities): Assess how effectively the organization verifies the identities of users and devices seeking access to its resources. This typically involves strong authentication methods, such as multi-factor authentication (MFA), to confirm the identity of users and devices.
- Least privilege access (Endpoints): Evaluate the extent to which the organization enforces the principle of least privilege. This means providing users, devices, and applications with only the minimum access required for their specific roles and responsibilities.
- Micro-segmentation (Apps and infrastructure): Analyze how well the network is segmented into smaller, isolated zones, allowing only authorized access between them. Micro-segmentation limits lateral movement within the network and is applied to both applications and infrastructure components.
- Continuous Monitoring (Data and network): Assess the organization’s ability to continuously monitor and inspect user and device behavior within the network. This includes real-time threat detection, anomaly detection, and the continuous monitoring of data and network traffic for signs of compromise.
- Data encryption and protection (Data and network): Examine how well data is protected both in transit and at rest. This pillar involves assessing the use of encryption protocols for securing data in transit and data at rest. Additionally, data protection measures, such as data loss prevention (DLP) technologies, should be in place.
To assess these pillars effectively, a combination of methods can be employed, including surveys and interviews with relevant teams, review of documentation, technical assessments, and compliance checks.
The ultimate goal is to gain a comprehensive understanding of how well the organization has implemented the zero-trust framework and to provide actionable recommendations for improving its security posture based on the assessment’s findings.
Example questions to assess zero-trust posture
When conducting a take-in assessment to evaluate how well a company has implemented a zero-trust security model, a cybersecurity consultant could present the following 10 questions in an assessment:
- Identity verification: Can you describe the organization’s approach to user authentication, and do you utilize multi-factor authentication (MFA) for user access?
- Least privilege access: How are user access permissions determined, and are users granted the minimum access necessary for their roles?
- Micro-segmentation: Are network segments defined and isolated to limit lateral movement and access between different parts of the network?
- Continuous monitoring: What measures are in place to continuously monitor network and user activity for signs of compromise or suspicious behavior?
- Data protection: Can you provide an overview of the encryption methods and protocols used for data protection, both in transit and at rest?
- Application access control: How do you manage and control access to critical applications, and what mechanisms are in place to prevent unauthorized access?
- Incident response readiness: Incident response readiness Is there a well-defined incident response plan that aligns with the zero-trust model, and how often is it tested?
- Endpoint security: Do you have visibility into the security of endpoints and devices, and are security updates and patches deployed regularly?
- Remote access security: Are network resources accessible remotely, and if so, what measures are in place to secure remote access?
- Compliance alignment: What steps have been taken to ensure compliance with relevant regulations and industry standards in the context of zero trust security?
These cyber security risk assessment template questions help a cybersecurity consultant assess the maturity of the company’s zero-trust implementation across various key areas, including identity verification, access controls, network segmentation, continuous monitoring, and data protection. The responses will help identify areas for improvement and provide a basis for recommendations to enhance the organization’s zero-trust security posture
What Pointerpro clients are saying




One tool to manage it all
Typically, a complex and expensive chain of IT tools is required to get from data collection to a thorough cyber security risk analysis and a professional report.
With Pointerpro you customize and adapt everything to your needs, in a single application.
Cyber security vs. cyber security compliance
Cyber security and cybersecurity compliance are related concepts. The primary focus of cybersecurity security is to protect an organization’s information technology (IT) systems, networks, and data from threats and vulnerabilities. It encompasses all the technical, administrative, and physical measures that an organization employs to safeguard its digital assets. Cybersecurity compliance, on the other hand, is primarily concerned with adhering to external regulations, standards, and industry-specific requirements related to information security. It focuses on meeting specific legal and regulatory obligations and industry best practices.
The goals of both are ultimately the same. However, the main objectives of cybersecurity are to actively prevent security breaches, mitigate security risks, protect sensitive data, maintain the confidentiality, integrity, and availability of information, and ensure business continuity.
Cybersecurity compliance, on the other hand, more directly aims to ensure applicable laws and standards are followed in order to avoid legal consequences, protect an organization’s reputation, and maintain customer trust.
Therefore the methods and responsibility for both tend to differ in an organization:
- Methods: Cybersecurity involves the implementation of security technologies, practices, and processes, such as firewalls, encryption, intrusion detection systems, access controls, and incident response procedures. Compliance often involves conducting audits, assessments, and evaluations to confirm that an organization’s security practices meet the specified regulatory or industry requirements. It may also involve reporting and documentation to demonstrate adherence.
- Responsibility: The responsibility for cybersecurity typically falls on IT and security teams, who design, implement, and manage security measures. Whereas compliance is typically a shared responsibility among various stakeholders, including legal, regulatory, and IT teams. Compliance officers and auditors play a crucial role in verifying adherence.
Example: NIST cyber security framework
NIST stands for the National Institute of Standards and Technology. It is a federal agency within the United States Department of Commerce. NIST’s mission is to promote and maintain measurement standards, as well as advance technology and innovation to enhance economic competitiveness and improve the quality of life.
NIST is known for its work in developing and publishing standards, guidelines, and best practices across various fields, including cybersecurity. NIST’s Cybersecurity Framework and Special Publications provide guidance and standards for securing information systems and data.
NIST cyber security example questions
NIST provides a wealth of resources, including a framework and a series of special publications to help organizations improve their cybersecurity posture. To check if an organization is compliant with NIST cybersecurity standards and guidelines, it can ask a series of questions and assess its practices against NIST’s recommendations. Here are some typical questions to consider:
- Has the organization adopted the NIST Cybersecurity Framework?: This framework provides a structured approach to assessing and improving cybersecurity. Organizations can start by asking if they have implemented the core functions: Identify, Protect, Detect, Respond, and Recover.
- Have you conducted a thorough risk assessment to identify and prioritize security risks and vulnerabilities?: Risk assessment is a fundamental part of NIST’s approach to cybersecurity. It’s essential to understand where your organization may be vulnerable.
- Do you have documented cybersecurity policies and procedures in place?: NIST emphasizes the importance of having well-documented policies, procedures, and guidelines to guide cybersecurity practices.
- Have you implemented access controls and identity management to ensure the right people have the right level of access to your systems and data?: NIST places a strong emphasis on access controls and identity verification to protect critical assets.
- Is there a robust incident response plan that outlines how to detect, respond to, and recover from cybersecurity incidents?: NIST guidance includes creating a well-defined incident response plan, which is crucial for effective cybersecurity.
- Are you regularly monitoring your systems and networks for signs of compromise and potential threats?: Continuous monitoring is a core principle in NIST’s approach to cybersecurity.
- Do you employ encryption for data in transit and at rest to protect sensitive information?: NIST provides encryption guidelines to ensure data protection.
- Have you performed vulnerability assessments and penetration testing to identify and address weaknesses in your infrastructure and applications?: Regular vulnerability assessments and penetration testing are in line with NIST’s recommendations for proactive security.
- Are you providing cybersecurity training and awareness programs for employees?: NIST emphasizes the importance of cybersecurity education for all employees.
- Do you review and update your cybersecurity practices and controls regularly, in line with NIST’s guidance?: NIST’s approach includes a cycle of continuous improvement and adaptation.
These cyber security risk assessment template questions can help organizations assess their cybersecurity compliance with NIST guidelines and identify areas where they may need to make improvements. It’s important to consult NIST’s specific publications and guidance documents for more detailed and tailored recommendations.
Create your cyber security risk assessment today
You may also be interested in
Recommended reading

How Connections In Mind benefits the community interest through a digital mindset and a longitudinal assessment
The fact that communities benefit from diversity should not be news to anybody. One type of diversity you may not

Vlerick Business School digitalizes entrepreneurship development with Pointerpro [case study]
What do a top-tier international business school based in the capital of Europe and Pointerpro have in common? At the

Attain Global: How to do psychometric tests right and build a cutting-edge international business [case study]
In many countries worldwide, the pursuit of skillful and engaged employees is not so much a war on talent as


