IT risk assessment template
What if you could build an IT risk assessment to assess and advise, accurately and objectively?
IT risk assessments are fundamental to improving operations and ensuring security for organizations.
Pointerpro is the 2-in-1 software that combines assessment building with personalized PDF report generation.
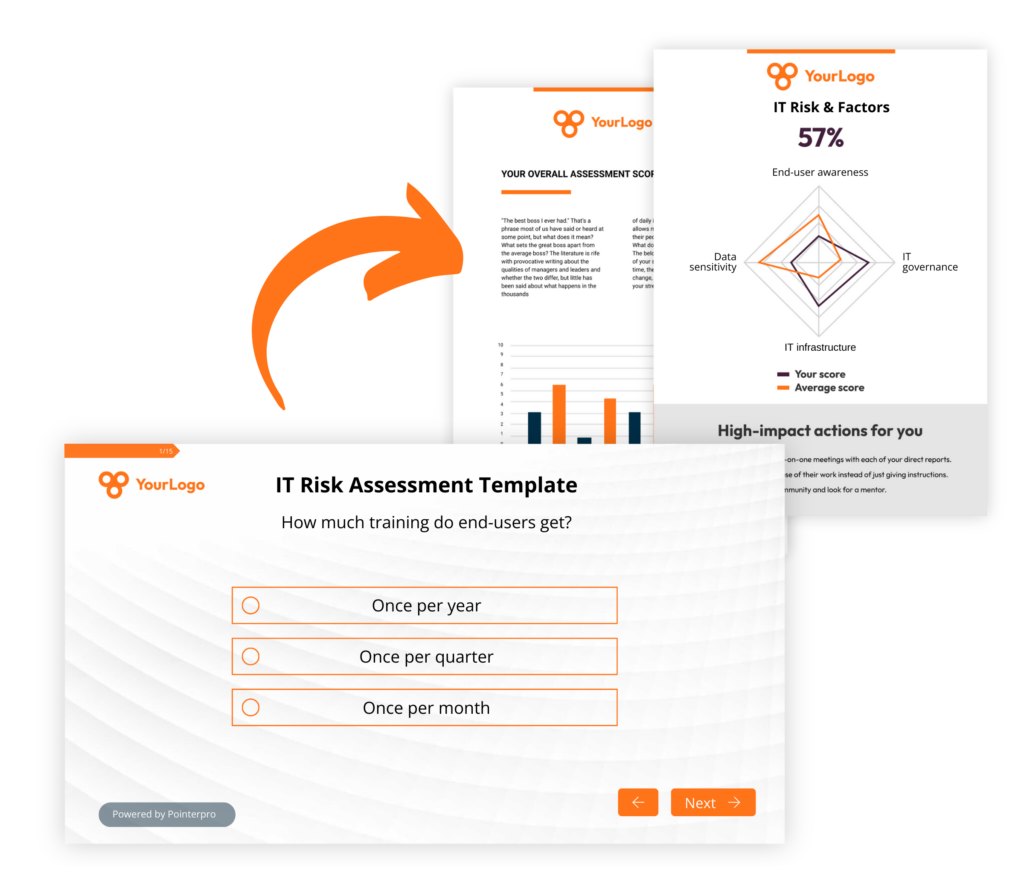
What is an IT risk assessment (template)?
An “Information technology” or IT risk assessment is a structured approach to identify, evaluate, and manage risks associated with an organization’s information technology (IT) infrastructure and operations. It involves analyzing the potential threats and vulnerabilities that could negatively impact IT systems and determining the likelihood and impact of these events. The primary goal of an IT risk assessment is to help organizations understand and mitigate risks to their IT assets, ensuring the confidentiality, integrity, and availability of data.
3 reasons to use Pointerpro as an IT risk
assessment tool
3 reasons to use Pointerpro as an IT risk assessment tool
Interactive user experience
With the Questionnaire Builder you get to create an engaging assessment. How? With numerous design and layout options, useful widgets and countless question types.
Refined, score-based analysis
Our custom scoring engine helps you quantify and categorize diverse IT risks. The result? An objective and nuanced assessment of your respondents’ answers.
Automated feedback in PDF
Thanks to your setup in the Report Builder, respondents instantly get a detailed PDF report: with helpful charts, a personalized IT risk analysis, and actionable tips
1.500+ businesses worldwide build assessments with Pointerpro








How to conduct an effective IT risk assessment
An IT risk assessment template is designed to systematically gather information from various stakeholders within the organization about their perception, understanding of, and/or influence on IT-related risks.
Be sure to guard over the following:
- Structured questionnaire: Have a set of predefined questions to probe different aspects of IT risk. These questions typically cover areas such as cybersecurity practices, data management, system access controls, compliance with IT policies, and disaster recovery plans.
- Broad participation: Distributed to a wide and diverse range of participants within the organization, including IT staff, management, but also end-users. This ensures a comprehensive understanding of risks from multiple perspectives.
- Risk identification: Be sure responses to the questionnaire help in identifying potential risks by highlighting areas of concern or weakness in the IT infrastructure and practices. An effective way is to provide multiple-answer options to which you attribute a score. Your assessment tool can quantify risks using formulas and score calculations.
- Risk prioritization: It’s important that based on the analysis of responses, risks are prioritized according to their potential impact and likelihood. This helps in focusing on the most critical risks that need immediate attention.
- Actionable insights: The results from the questionnaire should guide decision-making regarding where to allocate resources and what measures to implement to mitigate identified risks.
An IT risk assessment questionnaire is a tool for gathering insights and perceptions about the IT risk landscape within an organization. It is often used as a starting point for more in-depth risk analysis and management strategies.
20 IT risk assessment example questions
Here are 20 IT risk assessment example questions divided into 3 categories:
- 10 IT risk assessment questions
- 10 IT risk assessment to evaluate end-user awareness
10 IT risk assessment example questions
- How often are your IT systems audited for security vulnerabilities?
- Are there documented policies and procedures for IT security?
- Do employees receive regular training on IT security and data protection?
- Is there a process in place for managing and updating software patches?
- How do you manage access to sensitive data and systems?
- Are there regular backups of critical data, and are they tested for integrity?
- How do you ensure the physical security of your IT infrastructure?
- Are your network and data encrypted?
- How do you ensure compliance with relevant IT laws and regulations?
- Have you experienced any IT security incidents in the past year?
These IT risk assessment template questions are designed to assess various aspects of IT risk within an organization. They cover areas like system updates, incident response planning, employee training, access management, data backup, physical security, encryption, security audits, compliance, and past security incidents. Using a multiple-choice format will allow for a quick and structured evaluation of the organization’s current IT risk posture, helping identify areas that need attention or improvement.
What Pointerpro clients are saying




Is there a difference between IT risk assessment and cybersecurity risk assessment?
Both terms are often used interchangeably. The true difference between a cybersecurity risk assessment and an IT risk assessment lies primarily in their scope and focus, although they do overlap in several areas.
An IT risk assessment has a broader scope, encompassing all types of risks that can impact an organization’s IT infrastructure and operations. While cybersecurity threats are a significant part of this assessment, an IT risk assessment also includes other risks such as system downtime, hardware failure, software malfunctions, human error, and even natural disasters that could impact IT systems.
The goal of an IT risk assessment template is to evaluate the overall reliability, availability, and performance of IT resources, in addition to their security. It involves evaluating risks related to the physical IT infrastructure, software applications, data management, and compliance with broader IT policies and regulations. The IT risk assessment is not just about cybersecurity measures but also includes strategies for redundancy plans, backup solutions, maintenance schedules, and IT governance policies.
A cybersecurity risk assessment is a focused approach that specifically targets the identification, analysis, and mitigation of risks related to cyber threats. This type of assessment is primarily concerned with protecting digital assets from threats like hacking, malware, data breaches, and cyber espionage. It delves into the vulnerabilities in network security, software security, data encryption, and other areas that are susceptible to cyber-attacks.
5 often overlooked best practices to associate with your IT risk assessment
An IT risk assessment template is great to get started. However, IT risk management is a continuous cycle. Risk identification and even risk remediation aren’t the endpoint. Policies and risks evolve.
Though crucial, an IT risk assessment is only part of the cycle. Here are some other best practices that should be part of your risk management plan:
- Foster risk accountability among all employees: Cultivate a culture where every team member is aware of and accountable for managing risks. This practice embeds risk-aware thinking into everyday operations and nurtures a positive attitude toward risk management throughout the organization.
- Secure executive support for risk management: For your risk management strategy to be truly impactful, it's crucial to have an executive or high-level champion. Their backing ensures that risk management is prioritized and effectively integrated into organizational processes.
- Regularly update risk assessments: Consistently conduct risk assessments to maintain an up-to-date understanding of your risk or cyber risk profile. This ensures that business leaders have the latest information for making decisions that could affect the organization’s risk landscape.
- Assess and prioritize risks based on quantitative measures: Evaluate and rank risks by considering their likelihood, potential impact, and the cost of mitigation. This approach helps in allocating resources effectively to areas where they will yield the highest return, including in compliance efforts.
- Implement and manage risk mitigation strategies: Apply robust risk treatments that include stringent controls, measurable metrics, and effective management tools. This not only aids in continuous risk management but also actively reduces the most critical risks identified.
Who should be involved in the IT risk assessment process and why?
Involving the right stakeholders in the risk assessment process is crucial for its effectiveness and comprehensiveness. The process should ideally include a cross-functional team with diverse perspectives and expertise to ensure all aspects of risk are thoroughly evaluated. Key participants typically include:
- IT management and staff: IT managers and personnel have direct knowledge of the organization's IT infrastructure, software, and operations. They can provide insights into technical vulnerabilities, the current state of IT security, and operational risks.
- Cybersecurity experts: If available, cybersecurity specialists can offer in-depth knowledge on potential cyber threats, security protocols, and preventive measures against cyber attacks.It's often beneficial to involve external experts who can provide an unbiased view and specialized expertise in IT risk assessment.
- Risk management team: A dedicated risk management team, if present, can bring expertise in risk identification, analysis, and mitigation. They often have experience in conducting risk assessments and can guide the process methodically.
- Senior management and executives: Involvement from the top management is essential for aligning the risk assessment with business objectives and ensuring adequate resource allocation. Their support is also crucial for implementing any strategic changes based on the assessment's findings.
- Legal and compliance officers: Legal experts help in understanding regulatory requirements and legal implications of risks. They ensure that the risk assessment considers compliance with laws and regulations like GDPR, HIPAA, or other relevant standards.
- Department heads or business unit leaders: Leaders from various departments can provide insights into how IT risks might impact their specific operations. They can also help in assessing the feasibility and impact of potential risk mitigation strategies on business operations.
- Finance department: Involvement from finance professionals is important for understanding the financial implications of risks and for budgeting for risk mitigation measures.
- Human resources: HR's participation is important for assessing risks related to personnel and for planning training and awareness programs that support risk management efforts.
- End users or representatives from the user community: Input from end users can provide practical insights into everyday challenges and potential risks that might not be evident to management or IT staff.
By involving a diverse group of stakeholders, the risk assessment process can cover a wider range of perspectives, leading to a more accurate and holistic understanding of IT risks and their potential impact on the organization.
Common and emerging threats an IT risk assessment template should consider
- Cybersecurity attacks: This includes various forms of cyber attacks such as phishing, malware, ransomware, and denial of service (DoS) attacks. These attacks can lead to unauthorized access, data breaches, or disruptions in service, posing significant threats to data integrity and confidentiality.
- Data breaches and leaks: Unauthorized access and exposure of sensitive data, either through cyber attacks, employee negligence, or system vulnerabilities. Data breaches can result in significant financial loss, legal repercussions, and damage to an organization's reputation.
- Insider Threats: Risks posed by employees, contractors, or business associates who intentionally or unintentionally cause harm to the organization through misuse of access rights, theft of data, or sabotage of systems.
- Cloud security vulnerabilities: As organizations increasingly move to cloud-based services, vulnerabilities in cloud security become a significant concern. This includes issues related to data privacy, access control, and the security of shared cloud resources.
- Mobile device security: The use of mobile devices for business purposes introduces risks such as data leakage, unauthorized access, and the loss or theft of devices. Mobile device management (MDM) and security measures are crucial to mitigate these risks.
- Compliance and regulatory risks: Failure to comply with legal and regulatory requirements can lead to legal penalties, fines, and reputational damage. This includes regulations like GDPR, HIPAA, and others related to data protection and privacy.
- Third-party and supply chain risks: Risks associated with third-party vendors and suppliers, including breaches in their systems that can impact your organization, as well as risks related to their operational and financial stability.
- Advanced persistent threats (APTs): Sophisticated, long-term cyber attacks aimed at stealing information or disrupting operations, typically targeting high-value targets like government agencies and large corporations.
- Internet of things (IoT) vulnerabilities: The increasing use of IoT devices introduces new vulnerabilities, as many such devices have poor security features, making them easy targets for hackers to gain entry into broader networks.
- AI and machine learning exploitation: The misuse of artificial intelligence and machine learning algorithms to create sophisticated cyber attacks or to manipulate data and automated systems.
- Natural disasters and environmental risks: Events like earthquakes, floods, and fires can disrupt IT infrastructure and services. Preparing for these risks involves disaster recovery planning and data backup strategies.
Create your first IT risk assessment today
You may also be interested in
Recommended reading

Vlerick Business School digitalizes entrepreneurship development with Pointerpro [case study]
What do a top-tier international business school based in the capital of Europe and Pointerpro have in common? At the

Attain Global: How to do psychometric tests right and build a cutting-edge international business [case study]
In many countries worldwide, the pursuit of skillful and engaged employees is not so much a war on talent as
How youth development specialist Halogen reaches thousands of young Singaporeans with Pointerpro [case study]
Singapore, in Southeast Asia, is a global, economic powerhouse with a population of a little less than 6 million people.


