Security assessment template
What if you could build a security assessment tool to assess and advise, accurately and objectively?
Security assessments are crucial to safeguard the wellbeing of people and prevent various types of disruption for your organization.
Pointerpro is the 2-in-1 software that combines assessment building with personalized PDF report generation.

What is a security assessment?
A security assessment is a questionnaire that analyzes the security posture of an organization. The analysis may apply to different domains. Common ones are cyber security, information security, and of course physical security. It all depends on the organization using the assessment.
One thing all security assessment templates have in common? They critical for understanding the current measures in place. They identify potential vulnerabilities, threats and/or risks.
- Risk analysis: This involves identifying the various risks that could potentially impact the organization’s information systems. Risks can be due to various factors like cyber attacks, data breaches, system failures, natural disasters, etc.
- Vulnerability analysis: This step involves identifying vulnerabilities in the system that could be exploited by threats. It includes scanning for weaknesses in software, hardware, and processes.
- Threat analysis: This process involves identifying potential threats to the organization, such as hackers, malware, insider threats, etc., and analyzing the likelihood of these threats.
Other components of a security assessment, depending on the context:
- Impact analysis: Measuring the potential impact on the organization if a security breach or incident occurs.
- Security controls review: Analyzing the effectiveness of current security measures and controls in place. Some examples? Enforced policies, procedures and access controls.
- Compliance check: Ensuring that the organization’s security measures follow relevant laws, regulations, and industry standards.
Security assessments are typically conducted by internal experts or by external consultants specialized in the relevant security domains. A security assessment is only as good as the report and recommendations it generates. To produce high-quality security assessments and reports on scale, Pointerpro offers both questionnaire and report template building capabilities.
Security assessment vs risk assessment
What’s the difference between a security assessment and a risk assessment?
The terms “security assessment” and “risk assessment” are both used in the context of organizational security. Though often used interchangeably, they actually refer to different processes.
A security assessment covers the overall security posture of an organization. It concentrates on how well the organization protects its assets from various threats. A risk assessment is more focused. It specifically identifies, evaluates, and estimates the likelihood and impact of risks. In other words, a risk assessment could be a component of a broader security assessment. A security assessment template is like a map. A risk assessment is a zoomed-in view on specific areas of that map.
A security assessment should result in a comprehensive understanding of an organization’s security stance, along with recommendations for strengthening security measures and practices. Risk assessments identify and outline individual risks. They paint a picture of their likelihood to interfere with security and their potential impact.
3 reasons to use Pointerpro as a security
assessment tool
3 reasons to use Pointerpro as a security assessment tool
Interactive user experience
With the Questionnaire Builder you get to create an engaging assessment. How? With numerous design and layout options, useful widgets and countless question types.
Refined, score-based analysis
Our custom scoring engine helps you measure security for different domains. The result? An objective and very nuanced assessment of your respondents’ situation.
Automated feedback in PDF
Thanks to your setup in the Report Builder, respondents instantly get a detailed PDF report: with helpful charts, a personalized analysis, and actionable tips.
1.500+ businesses worldwide build assessments with Pointerpro








30 security assessment example questions
Here are 30 of the best risk assessment example questions divided into 3 categories:
- 10 facility security assessment example questions
- 10 supply chain security assessment example questions
- 10 environmental security assessment example questions
10 facility security assessment example questions
- Is there a formal security policy in place for the facility?
- Are there regular security training and awareness programs for the employees?
- Do you have access control systems installed at entry and exit points?
- Are surveillance cameras installed and actively monitored?
- Is there an emergency response plan in place for security incidents?
- Are there regular security audits and inspections conducted?
- Is visitor access to the facility controlled and monitored?
- Are fire safety systems (like smoke detectors and fire extinguishers) installed and regularly tested?
- Is there a system for reporting and responding to security breaches or incidents?
- Are there procedures in place for handling confidential or sensitive information in the facility?
These security assessment template questions help paint a comprehensive picture of the organization’s capability in protecting its physical premises from various risks and threats. Each question is designed to probe critical aspects of physical security, including policy adherence, employee awareness, control measures, surveillance, emergency preparedness, and information security.
The implementation of these elements are crucial in safeguarding the facility against unauthorized access, potential security breaches, and emergency situations. By answering these questions, an organization can gauge its current security status and identify areas that require improvement or immediate attention.
10 supply chain security assessment example questions
- Do you have a formal supply chain security policy in place?
- Is there a process for assessing the security measures of your suppliers?
- Are there established protocols for secure transportation of goods?
- Do you conduct regular security audits of your supply chain processes?
- Is there a system to monitor and manage the risk of theft or loss in transit?
- Are employees trained in supply chain security best practices?
- Do you have contingency plans for supply chain disruptions?
- Is there a process to ensure the integrity of goods received?
- Are cybersecurity measures in place for protecting supply chain data?
- Do you have a system for tracking and verifying the origin of products?
These security assessment template questions evaluate the security and integrity of an organization’s supply chain operations. They address various aspects of supply chain security, from policy implementation and supplier evaluation to transportation security and data protection.
Each question seeks to uncover how well the organization manages and mitigates risks associated with the complex processes of their supply chain. That includes the ability to handle disruptions, maintain the integrity of goods, and ensure secure data practices.
By answering these questions, an organization can identify potential vulnerabilities in its supply chain and take steps to fortify its security measures. This assessment is crucial for ensuring the smooth and secure functioning of supply chain operations, which are integral to an organization’s overall success and resilience.
10 environmental security assessment example questions
- How vulnerable is the local ecosystem to climate change impacts?
- What are the potential threats to water quality in the region?
- How well are natural habitats protected from human activities that could lead to biodiversity loss?
- What measures are in place to prevent and respond to environmental disasters such as oil spills or chemical leaks?
- How resilient is the local infrastructure to extreme weather events associated with climate change?
- Are there adequate waste management practices in place to prevent pollution and protect environmental health?
- What is the level of community awareness and engagement in environmental conservation efforts?
- How effectively are environmental regulations enforced to prevent illegal activities harming the ecosystem?
- Are there any invasive species posing a threat to the local flora and fauna, and what measures are taken to control them?
- How sustainable are current land use and development practices in relation to long-term environmental security?
These environmental security assessment template questions would typically be useful for government agencies, environmental organizations, community leaders, and researchers. They could employ an assessments on the basis of these questions to gauge the state of environmental security in a given area.
The environmental security assessment report that could come forth from these questions would be especially valuable to policymakers or local communities. The results could inform their decision-making processes related to resource allocation, regulation development, and disaster preparedness. Researchers could use the data to get a broader understanding of environmental security dynamics.
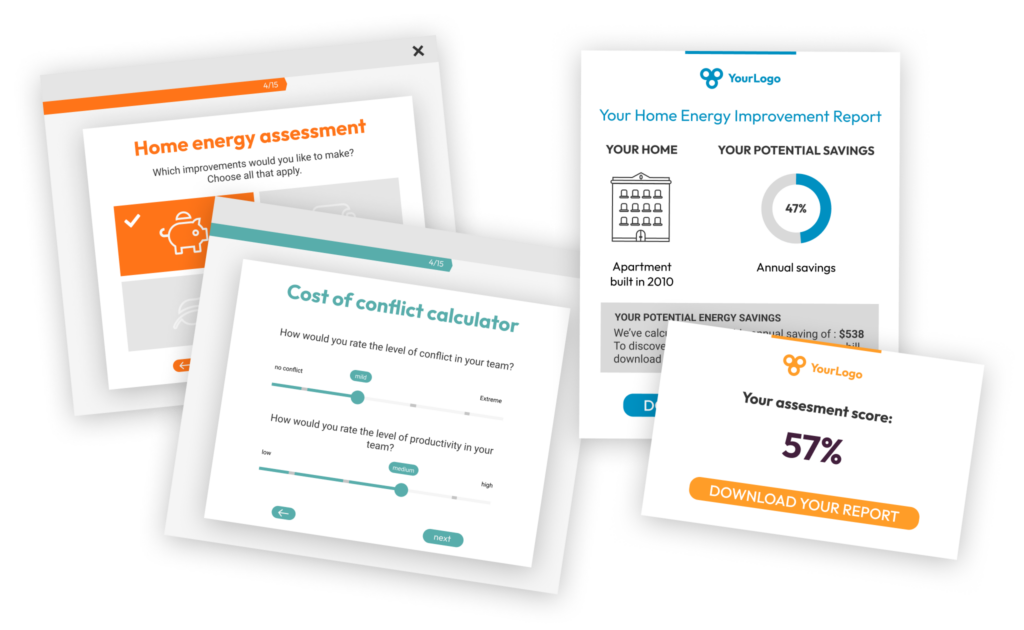
Automated scoring. Better insights
You apply formulas, so respondent input is calculated and measured.
The result? Relevant analyses, automatically molded into visual security reports for with feedback for respondents, but also aggregate reports for yourself and stakeholders.

What Pointerpro clients are saying




Raise your reputation with Pointerpro
Are you a consultant? Then you build your brand on the basis of your expertise.
With Pointerpro, you consolidate your know-how in a digital assessment tool to generate top-quality PDF reports on autopilot. And they deserve to carry your beautiful design and logo, don’t they?

Why a security assessment template PDF report is crucial
A security assessment report serves as a key document to encapsulate the assessment and its outcomes. It provides a comprehensive record of the security posture of an organization at a given point in time.
Why is it important? Because it translates a possibly complex evaluation into understandable and actionable information for respondents, who are very often non-experts. A good report not only details the current vulnerabilities and shortcomings but also offers a roadmap for addressing the issues. A formal PDF report also ensures accountability and transparency. It’s a documented trail for stakeholders to review and reference over time.
Moreover, a security assessment report serves as a communication tool. It bridging the gap between technical teams and management or other non-technical stakeholders, ensuring everyone is informed and aligned regarding the organization’s security status.
But building an effective, professional report takes time, doesn’t it? Yes, it does. But it doesn’t need to take time over and over again. As a security expert, using Pointerpro, you create your security report template only once, based on your knowhow and logic. From that point on, whenever someone takes the assessment, a personalized PDF report is generated based on the answers. The result? As a security consultant, you scale your activity with more ease, ensuring consistent quality.
How to create a security assessment report
Be sure to include the following in your report:
- Cover page: Begin with a cover page that includes the report’s title, the name of the organization, the date of the report, and a confidentiality notice or disclaimer.
- Table of contents: Follow with a table of contents for easy navigation through the report.
- Executive summary: This section provides a brief overview of the assessment’s purpose, key findings, and overall security posture, along with a summary of the major recommendations.
- Introduction: Describe the purpose and objectives of the security assessment, including the scope, which details the evaluated areas, systems, and processes evaluated.
- Methodology: Outline the methodology or framework your assessment is based on, along with the criteria and benchmarks for evaluation.
- Findings and analysis: Present a detailed account of the findings for each area assessed. This should include an analysis of identified vulnerabilities, threats, and risks. Use charts and visual representations to make the findings more easy to interpret.
- Risk levels: If measured, summarize and visualize specific risk levels (high, medium, low) for each identified vulnerability. Indicated potential impact and likelihood of associated risks.
- Security controls review: Evaluate the existing security controls, noting their effectiveness and identifying areas that lack sufficient controls.
- Compliance assessment: Assess compliance with relevant laws, regulations, and standards, highlighting any areas of non-compliance.
- Recommendations and action plan: Offer specific recommendations to address identified vulnerabilities and risks. Include a prioritized action plan with timelines and responsible parties for implementation.
- Conclusion: Conclude with final thoughts and a summary of the overall assessment.
- Contact information: Make sure that anyone who reads the report is able to interact with you about the results or follow-up action plan. Don’t forget to indicate contact information.
- Appendices: If available, include detailed data or supporting information such as audit logs, compliance checklists, and relevant diagrams or graphs.
The report should be clear, concise, and free of technical jargon. That way it’s accessible to both technical and non-technical stakeholders. As mentioned, visual elements like charts and graphs can be used for better data visualization. Dedicate suffiicent attention to the graphic design and branding of your report. Especially when you’re an external consultant this is important to evoke credibility.
Create your first security assessment today
You may also be interested in
Recommended reading

How Connections In Mind benefits the community interest through a digital mindset and a longitudinal assessment
The fact that communities benefit from diversity should not be news to anybody. One type of diversity you may not

Vlerick Business School digitalizes entrepreneurship development with Pointerpro [case study]
What do a top-tier international business school based in the capital of Europe and Pointerpro have in common? At the

Attain Global: How to do psychometric tests right and build a cutting-edge international business [case study]
In many countries worldwide, the pursuit of skillful and engaged employees is not so much a war on talent as